强网杯青少赛write up
EnterGame
先用DIE查壳,发现无壳后用IDA打开
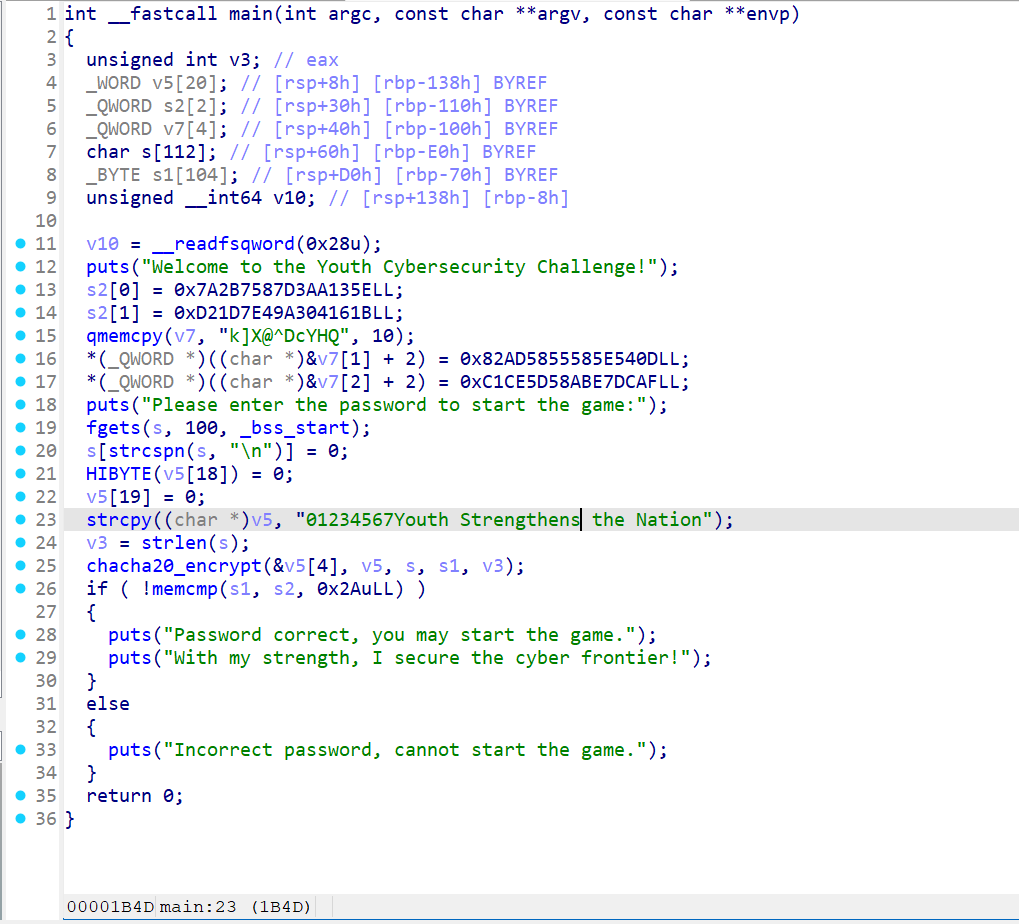
发现chacha20,是个对称密码,考虑直接patch输入密文
在判断的地方打个断点
直接动调
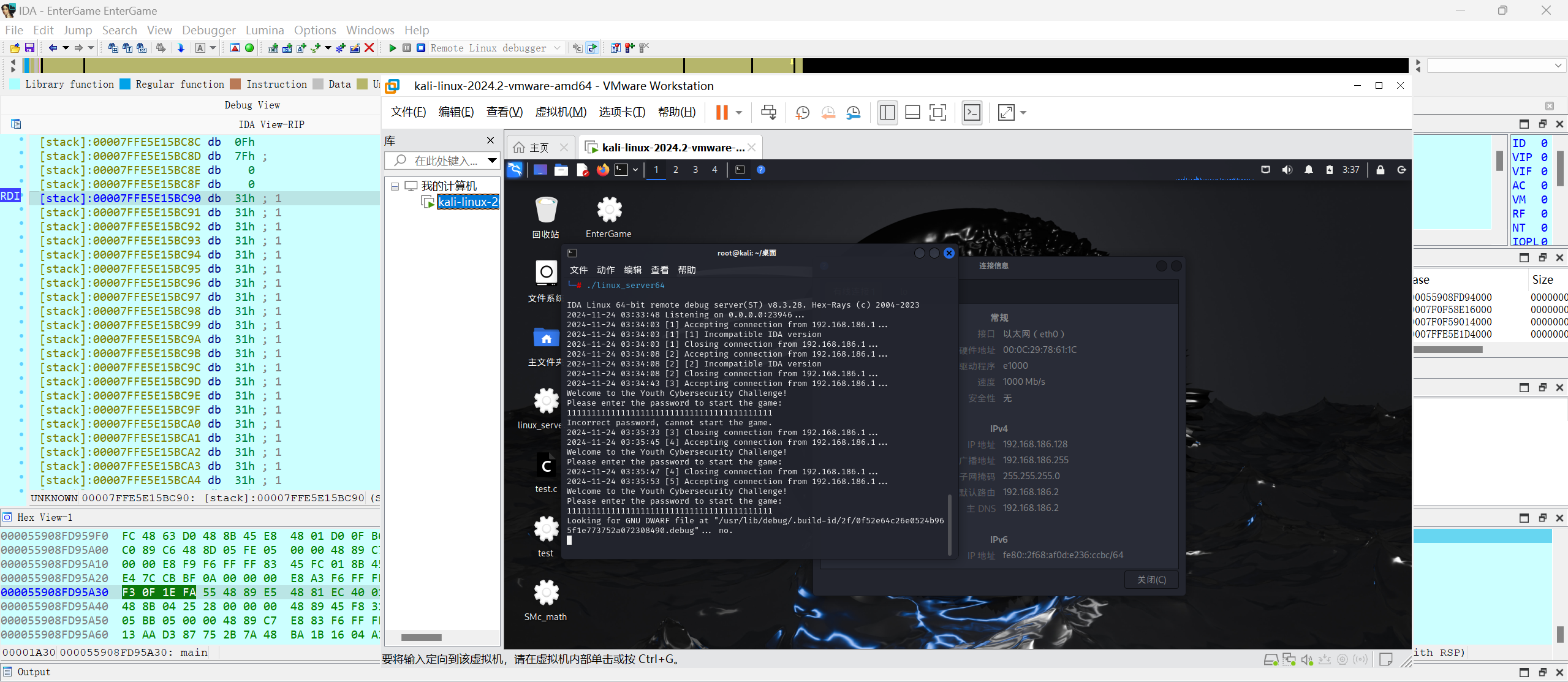
把密文patch输入
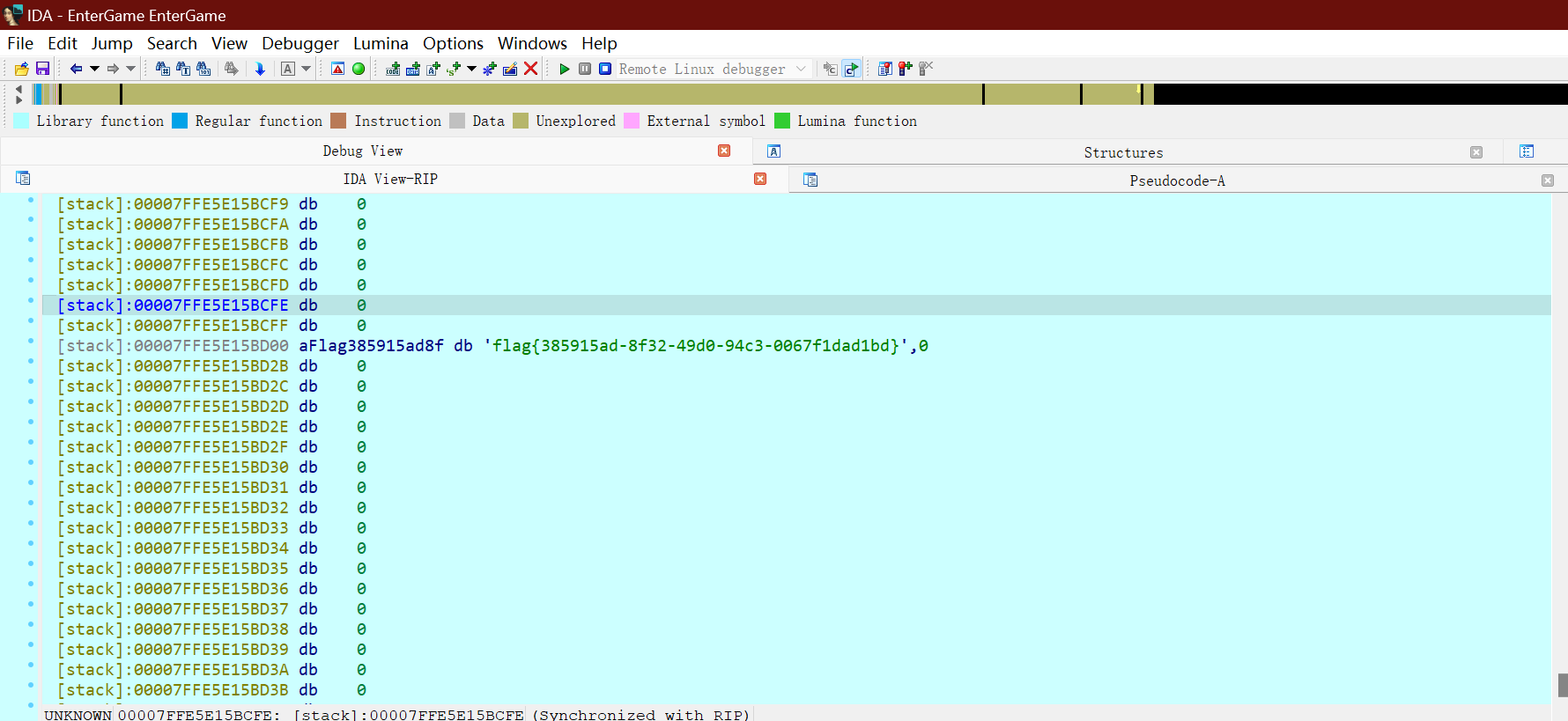
得到flag
Flip_over
下载附件用Jadx打开
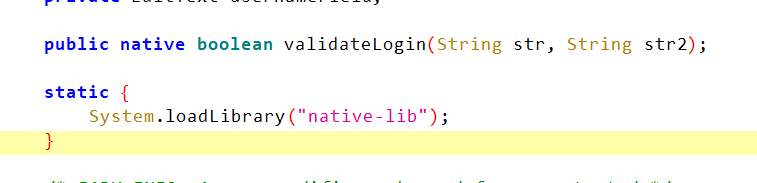
发现关键函数在native-lib里,用IDA反编译解包的so文件,可以发现加密逻辑是先过RC4,再过DES,最后再过一个异或,看了一下没有魔改,可以先用cyberchef处理之后再最后异或
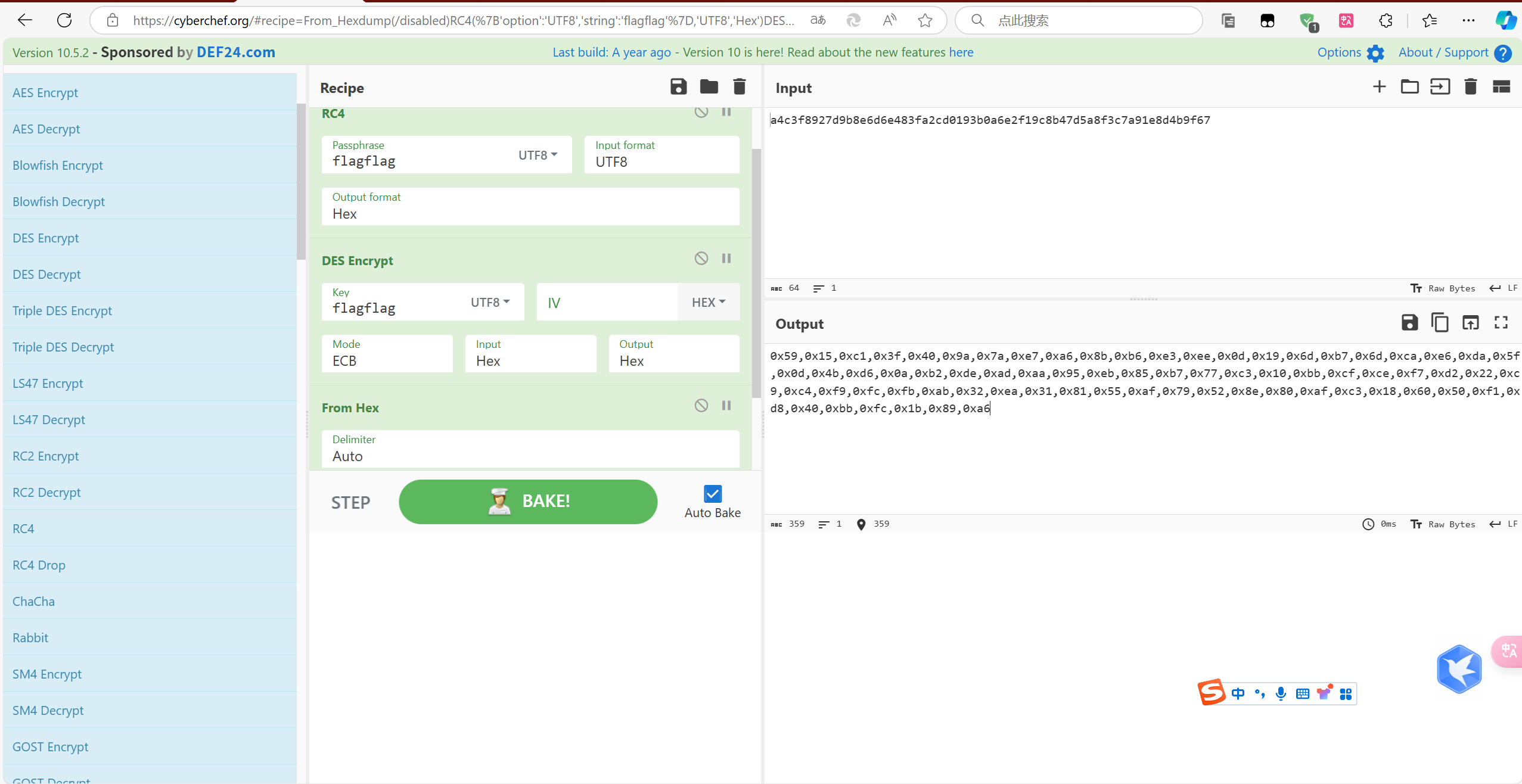
cipher1 = [0x59,0x15,0xc1,0x3f,0x40,0x9a,0x7a,0xe7,0xa6,0x8b,0xb6,0xe3,0xee,0x0d,0x19,0x6d,0xb7,0x6d,0xca,0xe6,0xda,0x5f,0x0d,0x4b,0xd6,0x0a,0xb2,0xde,0xad,0xaa,0x95,0xeb,0x85,0xb7,0x77,0xc3,0x10,0xbb,0xcf,0xce,0xf7,0xd2,0x22,0xc9,0xc4,0xf9,0xfc,0xfb,0xab,0x32,0xea,0x31,0x81,0x55,0xaf,0x79,0x52,0x8e,0x80,0xaf,0xc3,0x18,0x60,0x50,0xf1,0xd8,0x40,0xbb,0xfc,0x1b,0x89,0xa6] |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来源 Immey的观星台!

